
Who is Rhysida Ransomware?
Rhysida Ransomware Group is an emerging cyber actor threatening governments and critical infrastructure sectors throughout North America, South America, and Europe. The group first entered the digital landscape in May 2023 with an attack against the Government of Martinique, an overseas French collective in the Caribbean, and has since targeted over a dozen organizations.

How Does Rhysida Ransomware Operate?
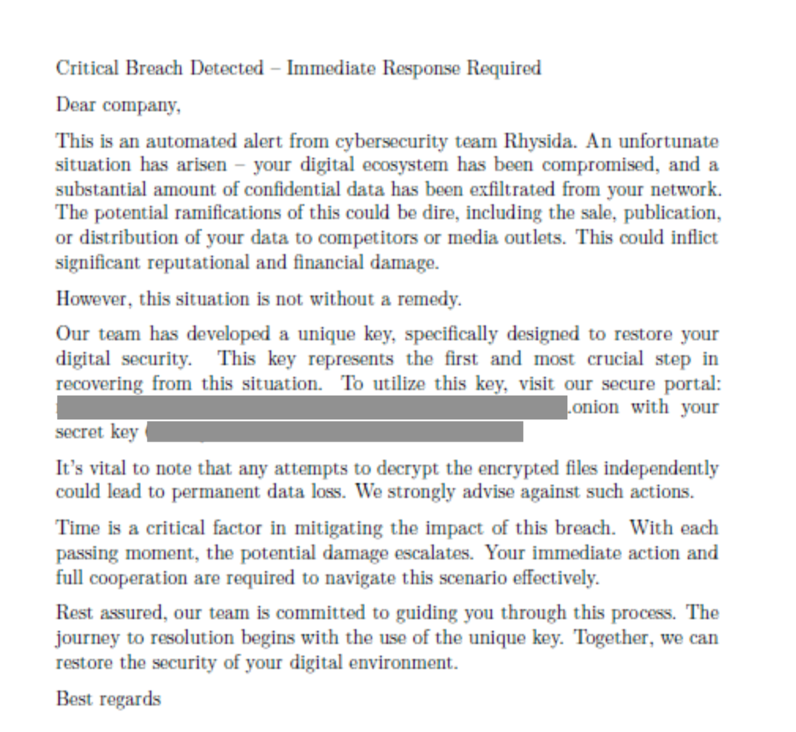
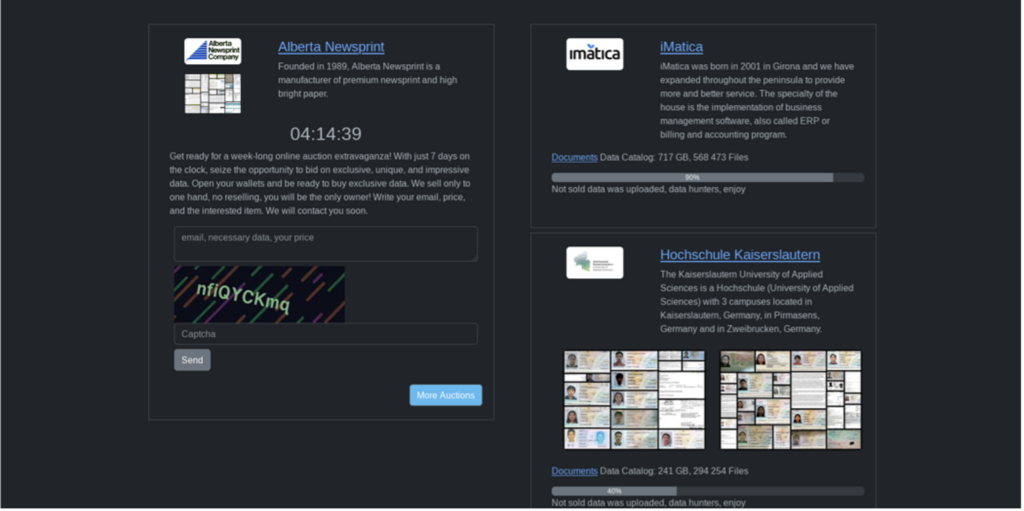
The group threatens victims with public distribution of their exfiltrated data via auction on their dark-web leak site, bringing them in line with modern-day double-extortionist groups. Rhysida requires payment in Bitcoin for the key to unlock their data. If payment is not received, Rhysida auctions the material off to “one hand.” They claim there is “no reselling, you will be the only owner.”
00055380 cmd[.]exe /c start powershell[.]exe -WindowStyle Hidden -Command Sleep -Milliseconds 500; Remove-Item -Force -Path
-d Path of directory to encrypt -sr Self-Remove
- \$Recycle.bin
- \Documents and Settings
- \PerfLogs
- \Program Files
- \Program Files (x86)
- \ProgramData\
- \Recovery
- \System Volume Information
Furthermore, the binary does not have the functionality to delete “VSS” Microsoft Volume Shadow Copies, which offer the ability to restore the system from backups.
Analysis of Rhysida
TeamWorx Security assesses Rhysida as novice and likely sources its code from other ransomware available in open-source repositories. The group likely pieces together multiple elements to create their package.
Following their attack against Lumberton Independent School District (ISD) & Stephen F. Austin State University (SFASU) in June 2023, the Daily Sentinel in Nacogdoches, Texas, received an email from Rhysida claiming responsibility for attacks and that SFASU was lying when the university reported they “did not believe any data was compromised.” In further emails, Rhysida revealed the amount and type of information stolen:
- “We downloaded about 1.2 terabytes of data from their (SFA) network, including SQL databases,”
- “Here an attachment that proves to you that we stole data. It’s basically a press release from an international gang.”
- “The same day we attacked SFASU, we also attacked the Lumberton Independent School District. They are withholding information about the attack. We downloaded 300 gigabytes of amazing personal documents and the proof is attached.”
The above analysis was made possible through collaboration in Hive-IQ and MATRIX. If you work for a .gov, .mil, or critical infrastructure and want to learn about these tools, contact su*****@**************ty.com.
- Threat Profile (Hive-IQ)
- Rhysida Sample (Hive-IQ)

Alex Lothstein
Alex is an Intelligence Analyst at TeamWorx Security. He has experience in the history/museum world researching, writing, and breaking down large pieces of information on complex topics into understandable bits for a general audience. His experience analyzing the past to better understand the present is a great asset in his intelligence research and writing.
-
Alex Lothstein#molongui-disabled-link
-
Alex Lothstein#molongui-disabled-link
-
Alex Lothstein#molongui-disabled-link
-
Alex Lothstein#molongui-disabled-link

John Rolley
John Rolley is a 26-year Army Veteran. He is an innovative Cybersecurity professional with a proven successful history in the Defense industry. John has compiled a unique set of skills and experience by fulfilling multiple work roles in cyber over nine years, spanning both offensive and defensive cyber operations. During this time, he has gained the knowledge, skills, and abilities in threat hunting, incident response, malware reverse engineering, and cyberspace operations planning.
-
John Rolley#molongui-disabled-link
-
John Rolley#molongui-disabled-link
-
John Rolley#molongui-disabled-link